Deliberate Learning
- Microsoft Azure Architect Technologies
- Microsoft Azure Architect Design
- Microsoft Azure Security Technologies
- To be a successful investor, you need to understand just two things:
- What to buy (depends on your ability to do fundamental analysis)
- When to buy and When to sell (depends on your ability to do technical analysis)
- Read the balance sheet of the company before investing in. Ensure the company is not violating fundamental rules of good finance management. (this is also useful to make career decisions either to join or leave the company)
-
Dopamine - The MOTIVATIONAL chemical
-
Oxytocin - The CONNECTION chemical
-
Serotonin - The MOOD & ENERGY chemical
-
Endorphins - The DE-STRESSING chemical
- Don’t force teenagers to wake up early. It’s counter productive
- Consider how long it takes for coffee to flush out from our body before thinking of another shot
- Lost sleep hours cannot be compensated with longer sleeps
- I get to read the book as collegues expect something every day.
- I also get to summarize what I have read (best method to retain knowledge is to share it).
- Collegues also get to read the book at a glance.
First solder in 30 years
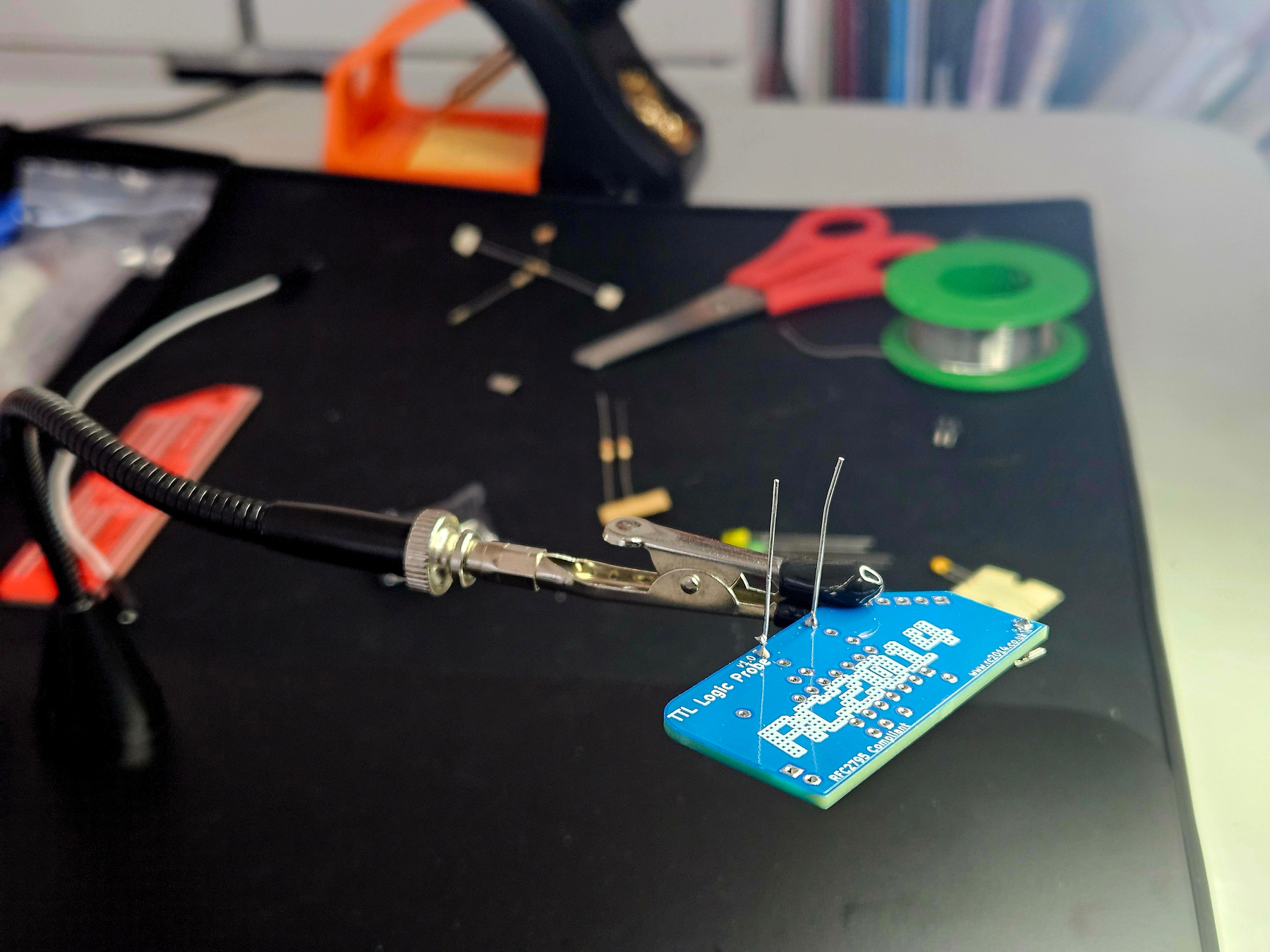
It’s nearly 1 month to this date when my daughter and I attended the RC2014 meet up in TNMOC in Bletchley. But it’s only today we chose to assemble the soldering kit and work table to do the start soldering. I had been reminiscing about this in my previous blog post, as a teen, on how I used to etch circuits on copper circuit boards and build a door bell.

This time we are assembling the 8 bit RC2014 computer. But before that I wanted to check if my eyesight can handle soldering. So we decided to practice soldering by assembling a cheap £5 kit - the TTL Logic Probe.
And yes, we did it. Was my daughter’s first ever solder and mine after 30 years. The soldering of the IC looked hard, so gave that piece to my daughter. We did not have 5v battery holder with 2-pin JST, instead we used the 3v battery holder that we got with microbit kit. It worked, and the happiness of having to see something glow after spending nearly 3 hours, is a great one.
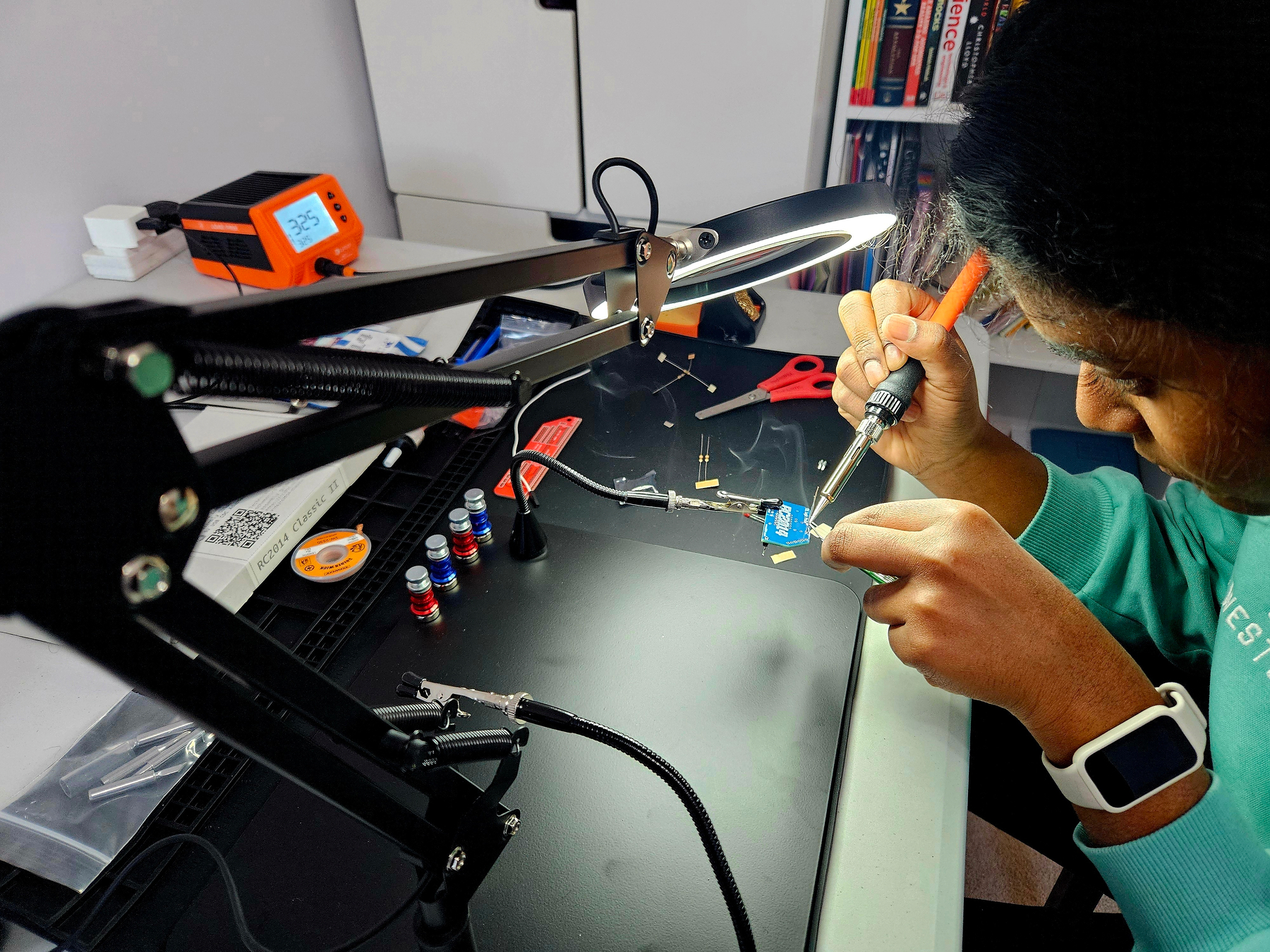
Learning by doing is a hard habit to get into. In my previous company we had some really good engineers who we totally into building 3D models, assembling split keyboards. Was fascinating to see them get time to do that back then, but I do realise now that time is available in plenty - we just have to spend it on doing what we love.

Coding with DNA
Today saw the return of me attending the friends of imperial lectures, that I used to never miss till about 4 years ago, since 2010.
The topic was just brilliant - Designing and Writing Synthetic Genomes to Advance Biology
At one point, when the audience asked what Tom Ellis, the professor, was quiet excited about, his obvious reply was the impact of AI and in the elaboration of that he mentioned how he was looking forward to create a prompt, with context and finesse the output of an LLM that produced Genetic Sequence. That was a jaw dropping moment for me.
It was also great to see the old acquaintance of members of friends of imperial, with whom I had visited CERN back in 2010.
Visiting Imperial college always leaves me with some inspiration and excitement about the future.

The Notebook of Data: A 50-Year Journey Behind TRUNCATE and VACUUM in Apache Spark
 When researching for my upcoming book on Data Engineering, I decided to trace back the origins of some of the most “taken-for-granted” operations in Apache Spark — things like
When researching for my upcoming book on Data Engineering, I decided to trace back the origins of some of the most “taken-for-granted” operations in Apache Spark — things like TRUNCATE and VACUUM.
At first glance, these commands seem mundane — one clears a table, the other cleans up old files. But when you go down the rabbit hole, you realize they are descendants of some of the most profound computer science ideas ever invented.
This post is my attempt to tell that story — through the metaphor of a humble notebook, and the decades of innovation that turned it into the high-performance distributed data engines we use today.
AI-102: More Than an Exam — A Map of AI Possibilities

I recently passed the Microsoft AI-102: Designing and Implementing an Azure AI Solution exam — though just by a whisker. It was one of those experiences that remind you how broad the AI landscape has become.
The toughest part wasn’t the theory. It was the sheer number of AI services you’re expected to know — what each one does, how they differ, and when to use them. Add to that a set of coding-style questions that test practical familiarity, and you realise: unless you’ve built and deployed solutions hands-on, the concepts alone won’t carry you through.
If you’re preparing for this exam, here’s what I found matters most:
Do the labs. Reading or watching videos won’t wire the knowledge into muscle memory. Spend time building solutions using Cognitive Services, Language Studio, Azure OpenAI, Custom Vision, and the rest.
Understand the why, not just the what. Every service exists to solve a slightly different problem — recognising when and why to use each is the key.
Expect real-world design questions. These scenarios force you to think like an architect, not a developer ticking boxes.
One side benefit — and perhaps the biggest value for senior engineers and tech leads — is that this exam serves as a catalogue of AI possibilities. You end up seeing the full spectrum of what can be built: from computer vision to conversational AI, from document intelligence to custom embeddings. It sparks new ideas for how to combine services into real solutions.
So yes, AI-102 is challenging. But if you treat it as an exploration, not an assessment, it becomes a creative journey — one that leaves you with both certification and inspiration.
From Data Solutions Architecture to Cybersecurity: A Journey of Continuity, Not Transition

My first foray into Application Security dates back to 2003, when I developed the Authentication and Authorization module for an ASP.NET 1.0 web application used by the State of Maine’s Center for Disease Control & Prevention for Breast and Cervical Health Screenings. That early responsibility—designing secure password storage mechanisms and implementing encryption—instilled in me the fundamental principles of security-by-design. It also gave me an enduring appreciation for the importance of protecting data at its very source.
In the years that followed, across the various public-facing websites I built and maintained, the OWASP Top 10 remained my trusted reference for web application security. Yet, it wasn’t until March 2019 that I became formally embedded within a Cyber Security division of a multinational enterprise. There, I gained a deeper appreciation of cybersecurity at scale—particularly in the context of securing global digital estates.
My team’s focus on Vulnerability Identification exposed me to one of the classic challenges in cybersecurity: asset discovery. Applying my Data Lake Strategy expertise, I helped create a security-tool-agnostic “Know Your Estate” solution, enabling visibility across thousands of assets. By leveraging “heartbeats” from multiple systems, we were able to establish a truthful and dynamic view of active hosts, forming the foundation for measuring coverage of intrusion detection systems such as CrowdStrike, Qualys, and Microsoft Defender.
A security consultant and close friend later told me that such innovation—bridging data architecture with security operations—was rare, as many enterprises focus mainly on compliance. That observation became a turning point, inspiring me to specialize further in cybersecurity while continuing to operate as a Cloud and Data Solution Architect.
To formalize this growing expertise, I pursued and earned a series of Microsoft certifications between 2020 and 2021, including:
From 2022 to 2024, while serving in senior leadership roles, my involvement deepened to encompass the implementation of security controls across the organisation. This extended beyond technical measures such as tenant-level IAM tightening to include process-level initiatives—for example, Cyber Awareness Training for Joiners and Movers and Attack Simulation exercises using Microsoft Defender.
My most comprehensive cybersecurity experience came during my tenure as Chief Technology Officer (CTO), where I led the organisation’s journey toward ISO/IEC 27001 certification. The one-year preparation involved drafting and operationalizing numerous security policies and procedures, embedding core security principles into every layer of the business. This culminated in the company achieving full ISO 27001 certification—a defining milestone that validated both our practices and my understanding of cybersecurity governance.
Having accumulated practical, leadership-level experience in implementing and governing cybersecurity programs, I felt it was time to formalize my expertise through professional certification. This led to my successful completion of the (ISC)² Certified in Cybersecurity (CC) certification—an important step in consolidating my knowledge and aligning it with globally recognized standards.
Whist I am continuing to architect, implement and deliver big-data scale data solutions for AppSec, my goal is to progress toward the CISSP certification, not as a career shift, but as a natural evolution of my ongoing journey—integrating data, cloud, and cybersecurity into a cohesive discipline aimed at securing information systems holistically.
Flirting with Stocks

Finished reading: Flirting with Stocks by Anil Lamba 📚
Two important take aways:
The DOSE Effect

Finished reading: The DOSE Effect by Tj Power 📚
The four chemicals:
Time is your enemy

Microsoft Fabric Data Engineer Associate certification : DP-700 exam
Having experienced this exam today, I can easily conclude that the biggest problem is not having enough time to answer all the questions.
Especially, if you are unlucky like me, to get the case study questions at the end of the exam instead of at the beginning - time just flies answering the first section. I was left only with 10 mins for the case study 🙁
So it’s more important to be fast in reading the questions. Most questions take long to read. If your first language isn’t English or you have difficulty reading fast in English, see if the exam is offered in your native language. I know for sure it’s available in Spanish and few other languages.
So don’t hesitate to take up the exam in your language of proficiency.
Good luck!
The Courage to Be Happy

Finished reading: The Courage to Be Happy by Ichiro Kishimi 📚
My fav topics
Life begins from incompleteness Civilisation is a product of the need to compensate for the biological weakness of the human being, and the history of the human race is the history of triumphing over its inferiority.
How many close friends do you have You cannot talk frankly about everything with a normal friend? Why can’t you take off the mask when you are with a “normal” friend.
From an ‘Art of Being Loved’ towards an ‘Art of Loving’ It is difficult to be loved by another person. But loving another person is a task of far greater difficulty
The Courage to Be Disliked

Finished reading: The Courage To Be Disliked by Ichiro Kishimi 📚
Some of my fav bits of wisdom from the book:
You’re the only one worrying about your appearance
Philosopher: Earlier didn’t your say, “I can’t celebrate other people’s happiness with all my heart'? You think of interpersonal relationships as competition; you perceive other people’s happiness as ‘my defeat’ and that is why you can’t celebrate it.
Overcoming the tasks that face you in life
Philosopher: The interpersonal relationships that a single individual has no choice but to confront when attempting to live as a social being - these are the life tasks. They are indeed tasks in the sense that one has no choice but to confront them. Philosopher: First, let’s look at the tasks of work. Interpersonal relationships of work have the easy-to-understand common objective of obtaining good results, so people can cooperate even if they don’t always get along, and to some extent they have not choice but to cooperate. And as long as a relationship if formed solely on the basis of work, it will go back to being a relationship with an outsider when working hours are over or one changes jobs.
How to separate tasks
Philosopher: One does not intrude on other people’s tasks. That’s all. Youth: Hmm. I don’t really get it. In the first place, how can you tell whose task it is? Philosopher: There is a simple way to tell whose task it is. Think, Who ultimately is going to receive the end result brought about by the choice that is made?
Why We Sleep

Finished reading: Why We Sleep by Matthew Walker 📚
Biggest learnings:
Another Foray into Functional Programming
VS2010 beta2 has come with F#. Not that I was not interested in Functional Programming before. I’ve had a go at Erlang nearly 6 months ago and must say that I loved it. But the prospect of Functional Programming with .NET CLR (or rather DLR) definitely gives F# a special place.
More over, the most familiar IDE of Visual Studio is simply wonderful. I must admit, I’ve not yet started doing my katas on F#, partly because the functional programming concepts need to be ingrained before moving ploughing ahead. So, watched a couple of interesting videos tonight.
Back to formal education
Oh…it is a awesome feeling to go back to school to study.
I am now enjoying what I had been waiting for nearly 1 year. I am devoting my full time to books and that too on .NET books which makes me feel good.
But, it is not easy to go back to full time study after working in the industry. The contrast is in the case of university, we tend to be very consious about what we are learning. In the industry the learning process is overall and not in depth. So, learning during working is remembered more than the learning at university. I could realize this during my first week of my classes in The University of Hull where I am in the .NET MSc in Distributed Systems Development course. I came to know about this course through a blog post which i am not managing to trace back. And now, I am just doing the kind of stuff I’ve wanting to do in the past. Some cool low level compiler stuff upto using xml web services.
Why not read a book for your collegues!
I have now originally copied an idea from my friend, Rick. The idea is on how to make myself read a book. Rick started by writing out snippets (in his own words) from a book he was reading. Not just writing it for himself, he was sending them as mails to the colleagues.
It so happened that for sometime such mails stopped which prompted me to mail him to ask about the proceedings. He said he shall continue doing it. Which makes him read the book.
I have also started to do something like that now. I am reading the “Essential .NET - The CLR” by Don Box. And not just that. In our internal forum, a new forum has been dedicated to this purpose. (email becomes cumbersome due to maintainance problems).
Advantages:
