Techie
- Microsoft Azure Architect Technologies
- Microsoft Azure Architect Design
- Microsoft Azure Security Technologies
- Foundation3 with default CSS
- Foundation3 with SCSS (Sassy CSS, which is the syntax used by SASS – "Syntactically Awesome Style Sheets". SASS is an extension of CSS3 which brings familiar programming concepts to CSS like variables, nesting of selectors, functions aka mixins)
- Opened the design of table1 using SQL Server Management Studio.
- Selected the last 4 columns.
- Ctrl+C.
- Opened the design view of table2
- Ctrl+V
- Collecting and Analysing Requirements
- Web Application Designing (not Graphic/Web Designing)
- Implementing
- Testing
- Deploying and Going live
- Introduction to LINQ-SQL
-
Understanding Data Context
-
Mapping Schemas to Classes
-
Inserting data
-
Deleting
-
Updating
-
Joins with LINQ-SQL
-
Working with NULLs
- Understanding When queries execute
-
Deferred loading of related entities
-
Querying wth Stored procs
-
Updating with Stored Procs
- Transactions
- A multi-tier design (mainly to separate presentation code from business logic)
- Support themes in presentation layer to switch designs easily at later stage.
- Object oriented business logic layer (BLL) (with business objects)
- Data access layer (DAL) to be independent of underlying database (to switch databases or even use XML files as data store at a later time)
- Data Transfer Objects (DTO) to pass data between BLL and DAL
- Maximum use of Data Binding at the presentation layer
First solder in 30 years
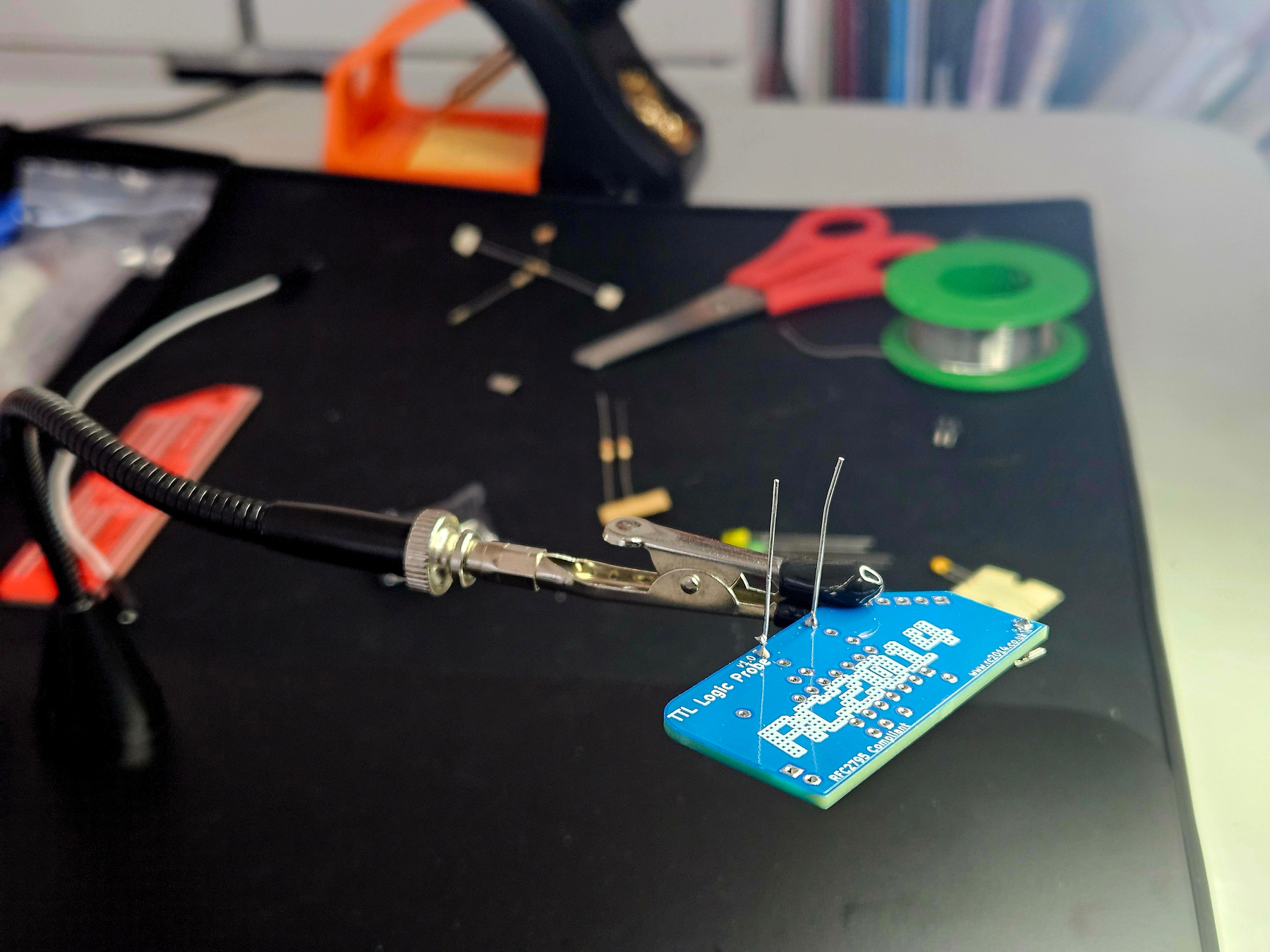
It’s nearly 1 month to this date when my daughter and I attended the RC2014 meet up in TNMOC in Bletchley. But it’s only today we chose to assemble the soldering kit and work table to do the start soldering. I had been reminiscing about this in my previous blog post, as a teen, on how I used to etch circuits on copper circuit boards and build a door bell.

This time we are assembling the 8 bit RC2014 computer. But before that I wanted to check if my eyesight can handle soldering. So we decided to practice soldering by assembling a cheap £5 kit - the TTL Logic Probe.
And yes, we did it. Was my daughter’s first ever solder and mine after 30 years. The soldering of the IC looked hard, so gave that piece to my daughter. We did not have 5v battery holder with 2-pin JST, instead we used the 3v battery holder that we got with microbit kit. It worked, and the happiness of having to see something glow after spending nearly 3 hours, is a great one.
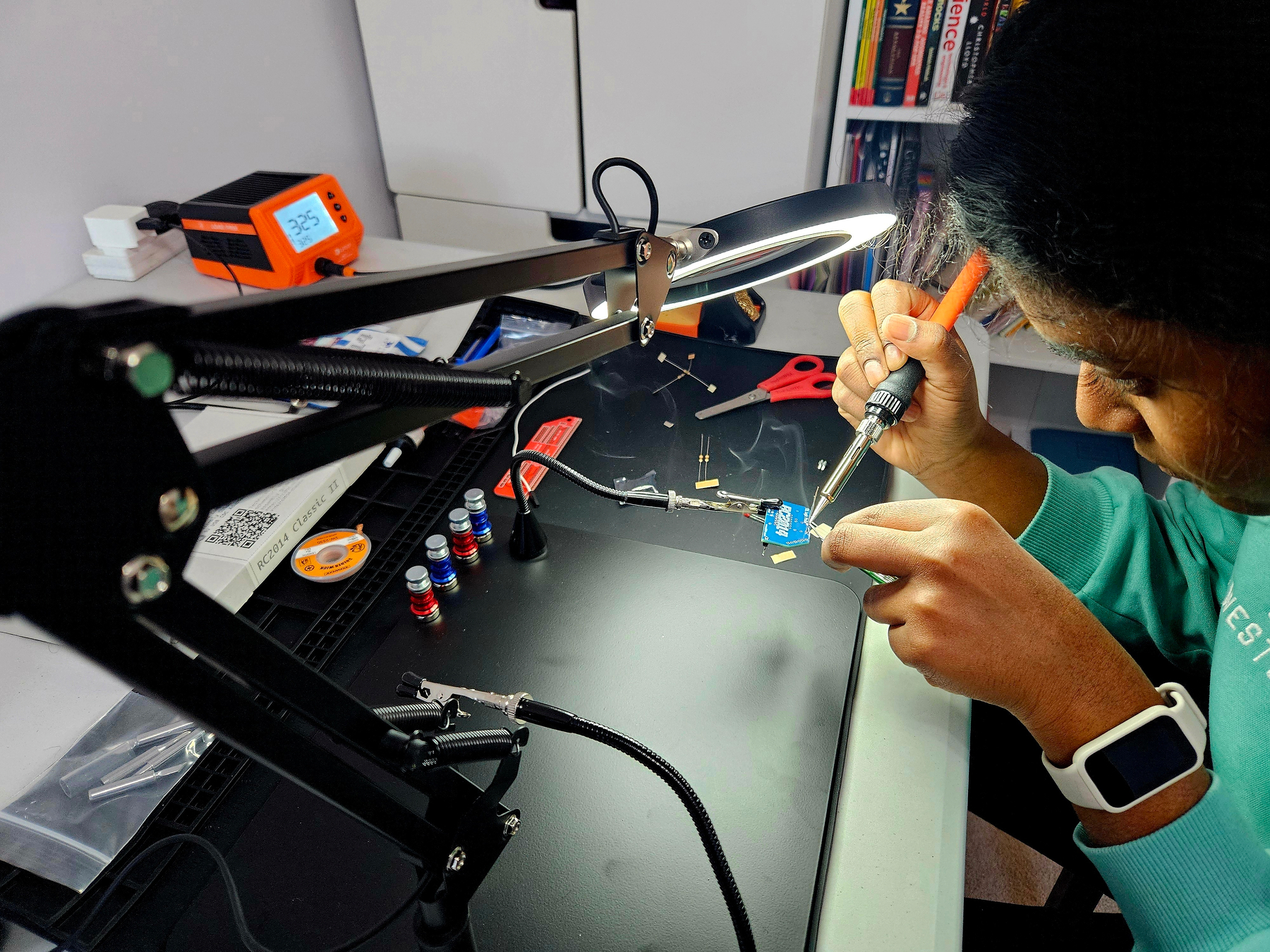
Learning by doing is a hard habit to get into. In my previous company we had some really good engineers who we totally into building 3D models, assembling split keyboards. Was fascinating to see them get time to do that back then, but I do realise now that time is available in plenty - we just have to spend it on doing what we love.

The Notebook of Data: A 50-Year Journey Behind TRUNCATE and VACUUM in Apache Spark
 When researching for my upcoming book on Data Engineering, I decided to trace back the origins of some of the most “taken-for-granted” operations in Apache Spark — things like
When researching for my upcoming book on Data Engineering, I decided to trace back the origins of some of the most “taken-for-granted” operations in Apache Spark — things like TRUNCATE and VACUUM.
At first glance, these commands seem mundane — one clears a table, the other cleans up old files. But when you go down the rabbit hole, you realize they are descendants of some of the most profound computer science ideas ever invented.
This post is my attempt to tell that story — through the metaphor of a humble notebook, and the decades of innovation that turned it into the high-performance distributed data engines we use today.
AI-102: More Than an Exam — A Map of AI Possibilities

I recently passed the Microsoft AI-102: Designing and Implementing an Azure AI Solution exam — though just by a whisker. It was one of those experiences that remind you how broad the AI landscape has become.
The toughest part wasn’t the theory. It was the sheer number of AI services you’re expected to know — what each one does, how they differ, and when to use them. Add to that a set of coding-style questions that test practical familiarity, and you realise: unless you’ve built and deployed solutions hands-on, the concepts alone won’t carry you through.
If you’re preparing for this exam, here’s what I found matters most:
Do the labs. Reading or watching videos won’t wire the knowledge into muscle memory. Spend time building solutions using Cognitive Services, Language Studio, Azure OpenAI, Custom Vision, and the rest.
Understand the why, not just the what. Every service exists to solve a slightly different problem — recognising when and why to use each is the key.
Expect real-world design questions. These scenarios force you to think like an architect, not a developer ticking boxes.
One side benefit — and perhaps the biggest value for senior engineers and tech leads — is that this exam serves as a catalogue of AI possibilities. You end up seeing the full spectrum of what can be built: from computer vision to conversational AI, from document intelligence to custom embeddings. It sparks new ideas for how to combine services into real solutions.
So yes, AI-102 is challenging. But if you treat it as an exploration, not an assessment, it becomes a creative journey — one that leaves you with both certification and inspiration.
From Data Solutions Architecture to Cybersecurity: A Journey of Continuity, Not Transition

My first foray into Application Security dates back to 2003, when I developed the Authentication and Authorization module for an ASP.NET 1.0 web application used by the State of Maine’s Center for Disease Control & Prevention for Breast and Cervical Health Screenings. That early responsibility—designing secure password storage mechanisms and implementing encryption—instilled in me the fundamental principles of security-by-design. It also gave me an enduring appreciation for the importance of protecting data at its very source.
In the years that followed, across the various public-facing websites I built and maintained, the OWASP Top 10 remained my trusted reference for web application security. Yet, it wasn’t until March 2019 that I became formally embedded within a Cyber Security division of a multinational enterprise. There, I gained a deeper appreciation of cybersecurity at scale—particularly in the context of securing global digital estates.
My team’s focus on Vulnerability Identification exposed me to one of the classic challenges in cybersecurity: asset discovery. Applying my Data Lake Strategy expertise, I helped create a security-tool-agnostic “Know Your Estate” solution, enabling visibility across thousands of assets. By leveraging “heartbeats” from multiple systems, we were able to establish a truthful and dynamic view of active hosts, forming the foundation for measuring coverage of intrusion detection systems such as CrowdStrike, Qualys, and Microsoft Defender.
A security consultant and close friend later told me that such innovation—bridging data architecture with security operations—was rare, as many enterprises focus mainly on compliance. That observation became a turning point, inspiring me to specialize further in cybersecurity while continuing to operate as a Cloud and Data Solution Architect.
To formalize this growing expertise, I pursued and earned a series of Microsoft certifications between 2020 and 2021, including:
From 2022 to 2024, while serving in senior leadership roles, my involvement deepened to encompass the implementation of security controls across the organisation. This extended beyond technical measures such as tenant-level IAM tightening to include process-level initiatives—for example, Cyber Awareness Training for Joiners and Movers and Attack Simulation exercises using Microsoft Defender.
My most comprehensive cybersecurity experience came during my tenure as Chief Technology Officer (CTO), where I led the organisation’s journey toward ISO/IEC 27001 certification. The one-year preparation involved drafting and operationalizing numerous security policies and procedures, embedding core security principles into every layer of the business. This culminated in the company achieving full ISO 27001 certification—a defining milestone that validated both our practices and my understanding of cybersecurity governance.
Having accumulated practical, leadership-level experience in implementing and governing cybersecurity programs, I felt it was time to formalize my expertise through professional certification. This led to my successful completion of the (ISC)² Certified in Cybersecurity (CC) certification—an important step in consolidating my knowledge and aligning it with globally recognized standards.
Whist I am continuing to architect, implement and deliver big-data scale data solutions for AppSec, my goal is to progress toward the CISSP certification, not as a career shift, but as a natural evolution of my ongoing journey—integrating data, cloud, and cybersecurity into a cohesive discipline aimed at securing information systems holistically.
DTUs, SUs, CU(s) - OMG!
There are a lot of units in Azure to forecast cost for various services. Yeah, even for pay-as-you-go in the cloud, a decent idea of projected cost is required to justify adoption of a new service.
The most recent for me was CU(s) in relation to Azure Fabric Capacity, which was indeed quite baffling. The usual mistake of thinking it must be something similar to other baffling units like DTUs, SUs etc, could cost us. Especially, as a start-up who have been given certain fixed credits by Microsoft for a year.
Thankfully, The Fabric Guy has written an amazingly detailed article on this matter and this should be a must read for anyone even uttering the word “Fabric”.
With that confidence of having understood what CU(s) (not CUs) are, it’s time to hit the road to get a real feel for it.
No more flickering of my 4K external screen
Finally after many years of frustration, managed to stop the flickering of my 4k monitor when it was connected to my surface book. Turns out that the setting in Edge “Use graphics acceleration where available” was the culprit. As soon as I turned it off, I think the built-in Windows algorithm that decides to switch the graphics card, stopped doing it and now, I have a peaceful screen helping me focus on building Semantic Data Model.
Making Git Bash, SSH only GIT Remote, Pageant dance together
Given a SSH only GIT Repo, was unable to git clone the repo, despite my public key being successfully stored in the remote repo’s authorization_keys file.
The git clone command invoked from within the git bash kept prompting for password, but could not authenticate for some bizarre reason. Thought it could be some proxy issue. But no, was able to ping successfully to the server hosting the git repo.
Then came the saviour. Pageant.exe, which gets installed when PuTTy SSH client gets installed in windows. Pageant runs on the system tray and serves like a vault of .ppk keys. After adding my ppk to it, was able to successfully connect to the server using putty. Then I thought git clone will also work. But No. Apparently an environment variable GIT_SSH pointing to plink.exe (found within the putty installation directory) is needed. After adding that, I was able to git clone the repository without it prompting me for a password.
Getting started with SaSS, Foundation, Compass on Windows, for PHP web application development
My friend wanted to get started with using Foundation for an upcoming Greenfield project. The trouble is Foundation comes in two flavours:
The Compass framework does not have a Windows Installer. It is only available as a Ruby Gem package, which means we have to install Ruby for Windows first. After this, we follow the following steps to get Compass with Foundation:
Start Command Prompt with Ruby (Run as Administrator)

Cross-Domain, Ajax Fundamental understanding
I had promised my students that we would implement a “Find nearest XXXX” feature in our on going project. I was doing this for the first time and thought it would not be difficult. But, most of my time while preparing for the class, I was frustrated.
I could not come up with a WCF Web Service (hosted on Visual Studio’s development web server eg., [localhost/MyService...](http://localhost:1234/MyService.svc) ) that could be invoked by Javascript on my website (hosted again on Visual Studio’s development web server eg., [localhost/MyWebsite...](http://localhost:9876/MyWebsite/Default.aspx) ).
Due to time constraints, I abandoned the WCF Service implementation and went in for the ASP.NET Ajax Page Methods
It’s only after reading this nice article, I understand the mistake I made or the way the cross-domain web requests work.
Mash-it Up with ASP.NET AJAX: Using a proxy to access remote API
ASP.NET MVC1.0 installer and VS2008 AddOns
Today I tried all things in vain to try and install ASP.NET MVC 1.0 on to my machine and it just kept failing.
Possible causes, upon Binging focused on conflicting Visual Studio 2008 addons. Among the list of such addons, I had PowerCommands. But, despite uninstalling it, mvc installer complained.
Then I begun uninstalling other possible addons (not listed in the mvc installer readme file). The first to go was SlickEdit gadgets.
Lo and behold, the MVC installation was successful.
Another Foray into Functional Programming
VS2010 beta2 has come with F#. Not that I was not interested in Functional Programming before. I’ve had a go at Erlang nearly 6 months ago and must say that I loved it. But the prospect of Functional Programming with .NET CLR (or rather DLR) definitely gives F# a special place.
More over, the most familiar IDE of Visual Studio is simply wonderful. I must admit, I’ve not yet started doing my katas on F#, partly because the functional programming concepts need to be ingrained before moving ploughing ahead. So, watched a couple of interesting videos tonight.
How to use Ninject IoC with ASP.NET MVC
The following are the detailed steps to use Ninject IoC with ASP.NET MVC
Download and install TortoiseSVN
TortoiseSVN is a Subversion client that allows you to manage source control tasks from within Windows Explorer.Download the source code for Ninject from google code
The Ninject source code is hosted in Google Code website. To download the code to PC, we will use TortoiseSVN. Before that we need the URL of the repository. This is available in the following url:TIP: Copy/Paste Columns to Multiple Tables in SQL Server
Here is a tip I discovered today while at work. I had earlier postponed the addition of common columns needed for all the tables (columns needed for auditing purposes like AddedDate, AddedBy etc.). But, the time had come now to type in and set the properties for columns on all tables one by one. I finished adding these columns to the first table. When on the second table, my laziness kicked in and wanted an easier way to do this mundane task. So,
Expression Blend 3 + SketchFlow + Dynamic Prototyping
One word: Incredible!
The Background:
I’ve got the privilege to work on a Greenfield project which involves:
Remote access of SQL Server from Host Machine
I use Vista running on a Virtual PC as my development environment (I used to use WinXP, but then came along Windows Azure which required either Vista or Win Server 2003). The usage of SQL Server Management Studio on the Virtual PC was slowing down the system. So, I wanted to use my Host Operating System to access the SQL Server using SQL Management Studio. By default the SQL Server engine is configured to minimise the surface of attack. So, remote access to the sql server engine is also not enabled.
To access remotely, the TCP/IP protocol needs to be enabled, using the SQL Server Configuration Manager.
LINQ-SQL Nuggeting
On my recent project, I had to help my co-developer get an understanding of LINQ-SQL (Yes, I am aware that LINQ-SQL has been shelved by M$).
I remembered the brilliant MSDN Nuggets that were produced by the evangelist teams here in Microsoft UK. These were helpful short videos organised by tags based on technology/interests. They are even now hosted in MSDN UK web site. But, they have a search facility instead of the earlier tags/categories. I generally don't lend myself to searching on MSDN despite it insisting "live search" with green coloured attractions. So, felt a bit disappointed at the difficulty in locating nuggets for a specific technology/interest.
I just opted to view all the nuggets by Mike Taulty. Eventually picked up the list of nuggets for LINQ-SQL that might be of immediate help to my co-developer.
Hope that helps my friend to get up to speed with this project.
Tapovanam - application design and architecture
In redesigning and redeveloping Tapovanam's (my friend's organisation) web site, I want to put in place a good architecture. The following are some of the considerations:
Web client software factory - Hands-on-lab
Having decided on giving the WCSF a try, I had a pretty smooth experience with installing WCSF.
The February-2008 release of WCSF does not use the Enterprise Library 4.0. It uses Enterprise Library 3.1. Although, the EntLib 3.1 is sufficient for WCSF-Feb'08, it just feels good to have and build upon the latest version. It took a few careful steps to get the WCSF working with EntLib 4.0. And even after that, at times, the guidance packages generate code that still uses EntLib3.1. This is not a major problem because I was able to re-reference the projects to the latest EntLib 4.0 assemblies.
The foremost concept to understand is the Modular structuring of the Web Application.
Then comes the understanding of Model-View-Presenter pattern. It took a while for me to figure out the role of Controller.
There is also the concept of a Service that gets consumed by a Controller. This Service has nothing to do with Web Services.
In fact, there is much more fundamentals to understand than I could discover in the hands-on-lab sessions.
The best resource (and by far the best writing) to explain concepts related to WCSF is Simon Ince's blog series. His posts made me understand the purpose of WCSF and have also inspired me on the various architectural considerations.
Excluding vwd.webinfo from adding to VSS from VS 2005
When I have a ASP.NET WebSite (NOT WebApplication), I notice the presense of vwd.webinfo in my VS 2005 solution. The problem is the annoyance when it shows as a new source control item. (with a plus sign next to the filename). So, when ever I do a “Pending Checkins”/“Checkin”, it is included as part of the pending items.
At the moment I am taking care to uncheck this file and then do the checkin.
But, it would be nice to have tell VSS to exclude this file (or set of files) from trying to add to VSS.
I’ve also thought about “exclude from this project” option in Solution Explorer within VS 2005, but then it adds a file called vwd.webinfo.exclude and then this shows up in pending checkins once again.
Using the VSS client, there is a facility to include FileTypes. To my surprise, the *.webinfo was not included but still the VS 2005’s VSS plug-in tries to add it.
I’ve never managed to get an solution to this problem yet. Hopefully something might turn out at a later time.
Learning to Program the Ruby way
Well, it should not to be mentioned under this blogspace. Nevertheless, for the fun sake of it, I started to learn computer programming (now that it’s been nearly 8 years since I wrote my first proper computer program using C ). A friend of mine introduced me to a book he was having as a gift to his dad (who is starting to program). This book is titled ‘Learn to Program’ and it should be sufficient to say that it belongs to the ‘Pragmatic Series’ from the Pragmatic Programmers.
The book is amazingly interactive. I laughed and smiled while learning to program using this book. The author has done a commendable job in writing this book in such an lucid manner.
And what can I tell about Ruby? From One-Click Download and Installation upto using the SciTE editor, everything was simple and neat. Not a single problem. The language is also very very light in appearance and does a good job. I am loving it every day. Looks like after a long time, the need for learning a language for fun has really brought some fruit. Ruby is fun. No doubt! I don’t have current plans to use it for my projects. But, I may consider it to create website using the Ruby On Rails MVC Web Framework.


